X-Ways
Capture: Successfully seize all hard disks, files, and RAM
for Windows 2000/XP* + Linux
|
|
X-Ways Capture
1.21
not updated any more for a long time
Complete description as a PDF document |
Specialized computer forensics tool for the evidence
collection phase of a forensic investigation which
captures Windows and Linux live systems. X-Ways Capture
gathers all data from the running computer e.g. on an external USB
hard disk, such that during the analysis even encrypted or
otherwise protected data can be examined that was unlocked at the
point of time when the system was acquired.
X-Ways Capture saves you from returning empty-handed after pulling
the plug and imaging
hard disks the conventional way when you discover that the relevant
files are encrypted! Plus you may be able to find passwords in main memory that X-Ways Capture dumps for you.
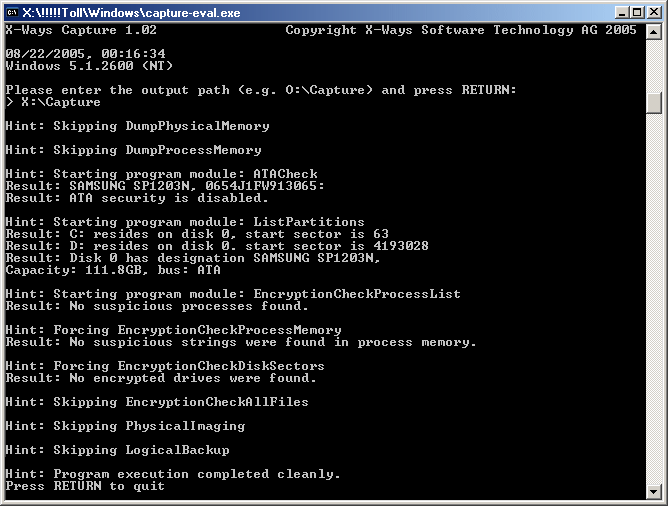
- Searches for indications of known or unknown
resident encryption software with different methods and reports them.
- Detects active ATA hard disk password protection.
- Dumps the physical RAM and the virtual memory of
all running processes.
- Acquires all connected media as either “dd” raw
images or evidence files/.e01 files (physical acquisition), either
mandatorily or depending on the results of the encryption and
password protection checks.
- Copies all readable files from all drives and
directories to the target disk (logical acquisition), either
mandatorily or depending on the results of the encryption checks.
- All steps and settings are fully user-configurable
in advance and can even
be completely enabled or disabled.
- You can expand the list of known encryption
software products that X-Ways Capture will detect.
- Creates a thorough log of all findings and actions.
Resident encryption software such as
“PGP Desktop” or “BestCrypt” can be detected by known program names or signatures.
Encrypted, but currently unlocked containers/virtual drives will be
successfully acquired when copying files logically. The same holds true for
NTFS/EFS-encrypted files that the logged-on user can read. Fully
encrypted hard disks (such as provided by software products like “SecureDoc”
or “CompuSec”) or fully encrypted volumes (such as used by TrueCrypt or
BitLocker) will be detected as such generically and successfully
acquired by physical imaging, if currently unlocked. X-Ways Capture
consists of two modules, one for Windows 2000/XP*, the other for Linux (Intel x86
architecture each). X-Ways Capture is a command line program
that utilizes little main memory. The language can be switch between
English and German. X-Ways Capture is easy to use because once you
have tailored its logic to your needs, it will always do all the
work for you on its own when on site.
Compared to X-Ways Forensics, the
specialties of X-Ways Capture are that it
- runs under Linux also, not only Windows
- runs preconfigured steps automatically without
additionally user interaction
- automatically detects various encryption
schemes/password protection
- can optionally based on that make an intelligent
choice about whether to acquire the system immediately and
automatically while still running
|
X-Ways Capture licenses earn you
loyalty points.
License agreement
The user needs to be aware of the
fact that attaching another medium to a running computer and executing
X-Ways Capture will slightly alter the system, at least a small amount
of main memory. To keep X-Ways Capture as small as possible, it was
designed without a graphical user interface. Like this it alters as little memory
upon loading as possible.
In order to safeguard protected data in a decrypted state, you have no other choice than putting up with such a minor alteration.
Also please note that from the point of view of the operating system a
hard disk may not be in an consistent state during a live acquisition
(e.g. because temporary files were being in use). Dumping physical RAM and physically
imaging media requires administrator/root rights.
*Known
limitations under Windows Vista and Windows 2008 Server:
DumpPhysicalMemory and HPACheck do not work.
Contribution from Mark McKinnon: “I
recently have been testing using capture accross the network. What I did
was map 2 network drives on a virtual server back to my machine and ran
capture and was able to image the virtual server sitting from my desk.
This could come in handy for having to image a pc when the person
resides accross the country in a remote office.
“What I did was create a batch file that maps 2 drives, one to the
executable directory of capture and the other to where I want the output
to go to, and then do a psexec.exe on it with the option to copy the
file to the computer. I know this is changing the system somewhat but
the nice thing is the file is small enough to reside in the $MFT and not
actually written to disk. The only other changes to the system is to the
registry and also the prefetch (if xp is being captured). I also created
a frontend using autoit so that you could put in the parameters to call
the batch program, there is no echo on the batch file so you cannot see
the admin password that is being used which is another bonus for
administrators who do not want to hand out a password.
“Just thought I would pass it along as a bonus to using capture that
makes it a excellent buy compared to buying other more expensive (much
more) packages to do remote imaging. I have attached the Autoit script
and executable and the batch files if you are interested. You can also
put them on your site as wel to show how to remote image a server/pc
(the script probably needs some help though).”
Download.
Related software:
X-Ways Forensics • Evidor • X-Ways Trace |
